Melinda Mays Bowman
Kathryn Cantrell
W. David Wimberly
Revision 6, January 2001
The Functional Specifications for the Natural Secured Menus Maintenance System (NSM-MS) document the functions and features of this system. The NSM-MS system is used to maintain the Adabas files necessary for applications that are developed using the Natural Secured Menus Architecture (NSM-A).
The Functional Specifications are prepared in order to provide a clear and concise definition of the system. This document is prepared initially to ensure that the system meets the intended needs and requirements of those requesting its development. On an ongoing basis, the specifications serve as the primary reference regarding the functions and use of the system. Errors or omissions should be brought forward as they are identified so that corrections can be made.
Early in the development of Natural 1.2 applications at the University of Arkansas, we reviewed the Command-Driven, Menu-Augmented architecture (CDMA) document developed by John Wheat at the University of Texas. We first decided to implement this design in the development of the General Ledger Front end for Financial Affairs. CDMA was also used in the development of the Student Inquiry System.
With the installation of Natural 2, we sought to improve and eliminate the shortcomings of the Command-Driven, Menu-Augmented design that we implemented in Natural 1.2. The new and improved design is the Natural Secured Menus Architecture (NSM-A). During the winter of 1988, the Financial Aid Tracking System was developed. This system was the first Natural 2 application at the university and the NSM architecture was incorporated into the FINAID design.
The NSM Architecture is also 'Command-Driven and Menu-Augmented' but includes other features. The NSM Maintenance System provides NSM Architecture applications an alternative method for performing security maintenance functions other than Software AG's Natural Security. The NSM design was developed to distribute security functions to the users and to simplify security maintenance. See the NSM Architecture functional specifications for complete information.
The purpose of the Natural Secured Menus Maintenance System is to provide maintenance facilities for the files used to establish users, applications, and the access parameters for applications which use the NSM architecture.
Note: The file VALUE-SECURITY is maintained by the NSM-MS system. However, since security by value maintenance will be different for each application, the maintenance for this file will be defined and developed as needed for each application.
These NSM files comprise the primary data requirements for the NSM Maintenance System. Since this application itself is an NSM Architecture application, the same files maintained by the application are required for its operation.
The NSM-MS system is developed in Natural using the Natural Secured Menus Architecture. Since the NSM Architecture is "command driven", anyone using the NSM-MS System is able to move from any function to any other function, within their security constraints, by entering the desired command. The basic screen format is the same for all functions within the system. The message line is where prompts, errors and warnings are displayed. The user can select the position of the message line as either the top or the bottom line of the screen. The title and program information, normally displayed as the second line of the screen, contains the program name, program level, function title, and the current date and time. This line will be temporarily overridden by confirmation messages following the completion of most activities. The next two lines are reserved for the display and entry of key fields, the inputs used to specify what data is to be operated on and what is to be done with it. The bottom two lines of the screen are reserved for displaying available PFkeys and their associated functions.
NSM-MS provides online maintenance to the files required to utilize the NSM architecture. This maintenance is performed by three separate groups of users based upon their normal role and function.
The application owners are established by associating up to five different desks with a specific NSM application. They typically will be positions within the department that have primary responsibility for access to the application's data. Up to five Computing Services personnel are assigned as the application as analysts. Desk Administrators are defined by the access privileges granted within NSM-MS, including value security definitions which designate the specific Budgetary Units for which they are responsible.
Application administrators (owners) will directly control access to the data viewed and maintained by their systems. Therefore, they will be primarily responsible for data security, not Computing Services.
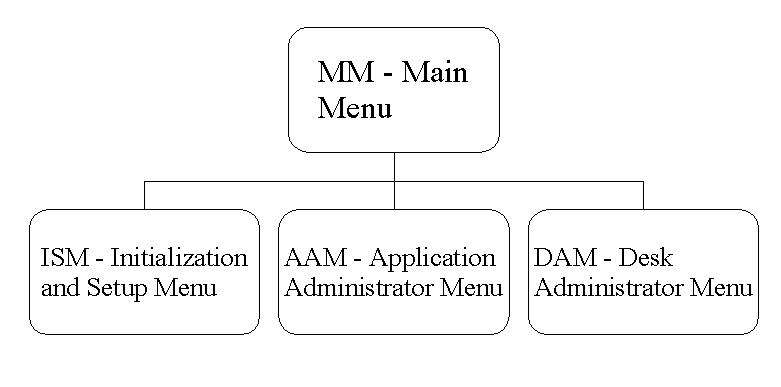
The commands available within the NSM-MS System can be divided by the functional responsibilities of Computing Services, application administrators, and desk administrators. Computing Services is responsible for maintaining Users, Applications, and Menu-Commands for all applications. The application administrators for a specific application are responsible for maintaining the access of desk to their application, command and value security groups, application notices, application locks, command security group locks, and command sequence lists. Desk administrators define and maintain desks as well as assign positions and users within their budgetary unit to these desks. The menu hierarchy for NSM-MS includes a main menu and three sub menus, one for each of these three types of users.
The following sections describe features and facilities of the NSM Maintenance System which apply to the entire application or are common to all functions.
Command security provides a means of restricting a desk or group of desks from accessing one or more commands within an application. This is accomplished by associating desks with a command security group and specifying which commands may be executed (allowed), which commands may not be executed (disallowed), or which commands will be executed with the designated security level with view only access granted to all non-listed commands (selective). Commands which are not available to a user are not displayed on the menus presented to that desk. Command security is inherent in all NSM Architecture applications.
The NSM-A also provides security levels which may be used to limit or restrict the functions performed within a command. The security levels allowed within the Natural Secured Menus Maintenance System follow. Security levels are enforced according to the order of the values, from most restrictive to most permissive.
| Level | Restrictions Enforced |
| 2 | Inquiry only with field restrictions |
| 4 | Inquiry only without field restrictions |
| 6 | Inquiry and Add only (cannot update existing records) |
| 7 | Update (cannot delete) |
| 9 | Delete |
Inquiry with field restrictions would allow a user to view a screen but selected fields would not be displayed. A restricted field in NSM-MS is USER-SSN.
Each desk of an application is assigned a security level by the application administrator. That value determines the maximum privilege that will be granted to the desk. Additionally, an administrator may designate a more restrictive security level for specific commands a desk is allowed to execute. The lower, more restrictive Security Level is always used. The NSM Architecture provides each function module (command) with the current security level, and, through common code, the application program interprets and enforces the restrictions associated with that security level.
The NSM Architecture provides security by value in a fashion similar to that of security levels. Value restrictions, if used by an application, are read from the VALUE-SECURITY file and provided to the application program. The value restrictions to be applied must be defined for each application and are unique to that application. Desks are associated with a group code which identifies a particular set of value restrictions. The restriction or enforcement of that security is performed at the function module (command) level and is the responsibility of each application.
NSM-MS incorporates this form of value security in the
maintenance of desks -- desk management functions may only be
performed when the operator has been authorized for the budgetary
unit associated with the desk and position or user. The system
also restricts the applications that may be operated on to those
users who have been identified as owners, or in some cases
analysts, of the application. Computing Services maintains data
in the APPLICATION, USER, and
MENU-COMMAND files. Departmental Desk administrators
define and update data for the DESK file, as well as
the assignments of desks to positions and users on the
DESK-ASSIGNMENT file. The application
administrators, or owners, update the information on the
APPLICATION-DESK file, establish the Command
Security Group and Value Security Group data, lock/unlock the
command security groups, and maintain application default access
ability and security. Application notices may be entered by
either owners or analysts of the application, and both groups may
also lock/unlock the application. The restriction of these
functions to only owners or analysts of an application is a
special form of value security that is built into the NSM-MS.
Online help is available at the application level, the screen or function level, and the element level. Access to each of these help facilities is as follows:
In addition to these system-wide help facilities, each specific function may provide additional help. Some functions provide the use of PF4 for DeCode. The de-code function will return descriptions associated with coded values on the screen or retrieve additional associated data. This feature will be described in the command description when it is available, and the PF4 function will be labeled on the bottom of the screen.
Complete documentation for the menus and online functions of the NSM Maintenance System is provided within this document. Menus are presented and then functions are listed in the sequence of their appearance on those menus.
The Main Menu is always the first screen displayed when entering the application. The complete menu appears in the Main Menu Figure, or view an actual image of the NSM Main Menu screen in a separate window. This menu contains the commands to access the three NSM-MS sub menus and the utility functions listed.
Enter, mark or position cursor to desired command
NSOMENU 1 TEST nsm maintenance system Main Menu - MM 01/08/01 16:30
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
CMD Command description Required key fields
---- ---------------------------------------- ------------------------------
_ LAAC List All Available Commands Command ID
_ MHAC Menu Hierarchy of Available Commands
_ DAM Desk Administrator's Menu
_ ISM Initialization and Setup Menu
_ AAM Application Administrator's Menu
_ CDCD Change desk/Display Current Desk info
_ LOG LOGon to another natural application
_ FIN FINish your session (sign off natural)
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Quit
|
The Desk Administrator's Menu contains the commands used to perform desk administration: defining desks, making desk assignments, and various list functions to display related information. The complete menu appears in the Desk Administrator's Menu Figure, or view an actual image of the Desk Administrator's Menu screen in a separate window.
Figure: Desk
Administrator's Menu
Enter, mark or position cursor to desired command
NSOMENU 1 TEST Desk Administrator's Menu - DAM 01/09/01 13:19
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
CMD Command description Required key fields
---- ---------------------------------------- ------------------------------
_ D Desk Desk
_ DA Desk Assignment Assignment Type, ID & Time
_ LDB List Desk for a Budgetary Unit Budgetary Unit & Desk
_ LUD List Users (desk assignments) for a Desk Desk & Time
_ LAD List Applications for a Desk Desk & Appl
_ LHDA List Historical Desk Assignments Assignment TYpe, ID & Time
_ LPBD List Positions for a BU and Date Budgetary Unit, Occ Cd & Date
_ LUU List User IDs for a User User
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Quit
|
This menu contains the functions used by Computing Services to define a new application or perform maintenance functions for existing applications. The complete menu appears in the Initialization and Setup Menu figure, or view an actual image of the Initialization and Setup Menu screen in a separate window.
Figure:
Initialization and Setup Menu
Enter, mark or position cursor to desired command
NSOMENU 1 TEST Initialization and Setup Menu - ISM 01/12/01 15:45
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
CMD Command description Required key fields
---- ---------------------------------------- ------------------------------
_ U User maintenance User
_ A Application maintenance Appl
_ M Menu maintenance Appl, Menu Cmd
_ LAA List Applications of an Analyst Appl, User
_ LVDB List Value sec grp for a Desk admin's BU Budgetary Unit
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Quit
|
The User maintenance, screen 1 figure is an example of the first screen of the User maintenance function, or view an actual image of the first User maintenance screen in a separate window.
Figure: User
maintenance, screen 1
Press PF8 to view next screen or enter new keys
NSOU 1 TEST User maintenance - U 01/12/01 16:06
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm: User: WDW
-------------------------------------------------------------------------------
Action: V User ID: WDW Screen 1 of 2
Status: A
SSN: 465-96-2408 Emp ID: 128828 on Employee
Name: Wimberly, David
Name: Wimberly, David
Last Comma First and Middle
BU: COMP Computing Services (Sync'd up monthly)
Case Translation: L
Entered: Updated: 09/01/00 by: WDW
David Wimberly
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode NextS
|
To add or update a user, enter or replace valid values for the required fields. To view, only the desired User ID is necessary. PF10 is required to confirm Actions A and U.
This is a two screen function. The first screen contains user attributes that are maintained by the system administrator. The second screen contains optional elements that may be maintained by the user through the user profile (available from the LOGON application). The field validations and special processing associated with the second screen are documented separately.
The remaining sections address:
The following edits are performed on the input data for screen one. Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A |
User ID must not exist on the USER file and must not already exist on the NATURAL-SECURITY file. |
|
V,U |
User ID must exist on the USER file. |
|
A,U |
Status must be A (Active), I (Inactive), or T (Temporary). |
|
A,U |
SSN must uniquely identify a record on the USER file if the ID's status is A (Active). |
|
A,U |
User Name must be non-blank and contain only alpha characters, one comma, periods or dashes. User Name is in the format last name, comma (required), first and/or middle names or initials. |
|
A,U |
Case Translation, if entered, must be either 'U' (Upper) or 'L' (Lower). |
|
Action |
Special Processing |
|
A |
Case Translation is defaulted to 'U'. |
|
A,U |
The User Name is not translated to upper case on input. |
|
A |
The User is added to Natural Security. |
|
V |
User SSN is a restricted field and will be conditionally displayed based upon the security level in effect (must be greater than 2). |
|
Action |
Effect on Data Base |
|
A |
A new record is stored on the USER file with the corresponding logical field assignments. Additional assignments include: DATE-OF-ENTRY and DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
U |
The existing record on the USER file is updated with the corresponding logical field assignments. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
The User maintenance, screen 2 figure is an example of the second screen of the User maintenance function, or view an actual image of the second User maintenance screen in a separate window.
Figure: User
maintenance, screen 2
Please enter new key fields
NSOU 1 TEST User maintenance - U 01/12/01 17:00
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm: User: WDW
-------------------------------------------------------------------------------
Action: V User ID: WDW Wimberly, David Screen 2 of 2
Email Address: wdw@comp.uark.edu
CMS ID: DW85047 @ UAFSYSB Campus Mail Bldg: ADSB Room: 220
Print Dest: A-DW85047 Default Application:
PF-Key Format N Message Line: T Terminal Type: 3279
Color Assignments for 3279 terminals:
Modifiable: Protected:
Default Intensity: GR NE PFKey Name: GR
Intensified: TU YE PFKey Function: TU
Reverse Video: GR NE Message Line: RE
Underline: TU YE Override Flag: N (Y/N)
NSM Field options: Modifiable default: V Color: NE
Modifiable intensified: V YE
Conditionally protected: D TU
Previous value: V GR
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit PrevS NextR
|
Screen two of the User maintenance function is used to view or maintain user profile parameters. This is an optional screen and contains the same elements also maintained by the user profile function available at LOGON.
The remaining sections address:
The following edits are performed on the input data for screen two. Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A,U |
If CMS id is entered, it must be the complete id, including the node (e.g., UAFSYSB). |
|
A,U |
PF-Key format must be either 'N' or 'S'. |
|
A,U |
Terminal type must be '3270', '3278', or '3279'. |
|
A,U |
Message Line position must be either 'T' or 'B'. |
|
A,U |
Color assignments for all field types, message line, and PF-Keys are available only for 3279-type terminals. If entered, the color entered must be one of the Natural color codes: BL, GR, NE, PI, RE, TU, and YE. |
|
A,U |
The Override Flag, to override program assigned colors with those defined by the user, must be either 'Y' or 'N'. |
|
A,U |
The attribute code for NSM fields must be one of the Natural attribute codes: D, V, I, U, C, or B. |
|
Action |
Special Processing |
|
A |
Default values for the user profile are established as follows: Terminal type is '3270', PF-Key format is 'N', Message line position is 'T', NSM modifiable default fields' attribute is 'V', NSM modifiable intensified fields' attribute is 'I', NSM conditionally protected fields' attribute is 'D', and NSM previous value fields' attribute is 'V'. |
|
A,U |
When the user enters color codes and field attributes, the corresponding fields on the screen which are defined with those attributes reflect the user's choices. For example, when a user selects the color code 'BL' for the PF-Key name and presses ENTER, the PF-Key names at the bottom of the screen are displayed in Blue. |
The Application maintenance, screen 1 figure is an example of the first screen of the Application maintenance function, or view an actual image of the first Application maintenance screen in a separate window.
Figure: Application
maintenance, screen 1
All entries are valid, press PF10 to Save
NSOA 1 Application maintenance - A 01/11/94 17:06
Command: Action: U Desk: Appl: NSM-DEMO Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
Action: U Application ID: NSM-DEMO Screen 1 of 2
Application Name: NSM Demonstration Application
Owner
Desk ID Desk Name Analyst Analyst Name
CHAOS Converted for W. David Wimbe WDW Wimberly, W. David
AVERNUS Converted for Kathryn Cantre
ASTRAEA Converted for Lonnie Deavens
ATLAS Don Barnett
Library: NSM-DEMO Application Lock: U X NSM Application
Application Prefix: ND Application Prefix for Predict 'Fields':
Value Security Maintenance Program: Main Menu Command: MENU
Entered: 08/03/92 Updated: 10/28/93 By: KATHRYN
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt NextS Save
|
The Application maintenance function is used to add, view, update or delete information about Natural Applications. The permitted Action codes are: A, V, U or D respectively. Values for Application ID and Action are always required. To add or update information for an application, enter or replace valid values for the required fields. To view or delete, only the desired Application ID is necessary. PF10 is required to confirm Actions of A, U or D.
This is a two screen function. The first screen contains the primary application attributes. The second screen is used to define security levels and action attributes for NSM applications. The field validations and special processing associated with the second screen are documented separately.
The remaining sections address:
The following edits are performed on the input data for screen one. Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
V,U,D |
Application ID must exist on the APPLICATION file. |
|
A |
Application ID must not exist on the APPLICATION file. |
|
A,U |
Library is required. |
|
A,U |
Application Name must be non-blank. |
|
A,U |
Owner Desk IDs must be valid desks, and Analyst IDs must be valid users. |
|
A,U |
At least one valid Owner Desk ID and one valid Analyst ID are required. The primary owner responsible for the Application should be entered as the first Owner Desk ID and similarly for Analyst. |
|
A,U |
Application Prefix and Main Menu Command are required if the NSM Application switch is set to true. |
|
D |
No references to this application must exist in the MENU-COMMAND, APPLICATION-DESK, COMMAND-SECURITY, or VALUE-SECURITY files. |
|
Action |
Special Processing |
|
A |
The NSM Application switch defaults to true. |
|
A,U |
Application Name is not translated to upper case on input. |
|
A,U |
Whenever an Owner Desk ID is entered, all of the Owner IDs' Names are retrieved from the DESK file and displayed. |
|
A,U |
Whenever an Analyst is entered, all of the Analysts' Names are retrieved from the USER file and displayed. |
|
V,U,D |
When PF4 is pressed, all the Owners' names, Analysts' names, and the Last Updated By name are retrieved from the appropriate files and displayed. |
Data base changes are only performed if all data is valid and PF10 is entered.
|
Action |
Effect on Data Base |
|
A |
A new record is stored on the APPLICATION file with the corresponding logical field assignments. Additional assignments include: APPLICATION-LOCK = U, DATE-ENTERED = current date, DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
U |
The existing record on the APPLICATION file for the specified Application ID is updated with the corresponding logical field assignments. Additional assignments include DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
D |
The record on the APPLICATION file for the specified Application ID is deleted. |
The Application maintenance, screen 2 figure is an example of the second screen of the Application maintenance function, or view an actual image of the second Application maintenance screen in a separate window.
Figure: Application
maintenance, screen 2
All entries are valid, press PF10 to Save
NSOA 1 Application maintenance - A 01/11/94 17:06
Command: Action: U Desk: Appl: NSM-DEMO Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
Action: U Application Id: NSM-DEMO Screen 2 of 2
Security 1 = View Act Action Desc MSL Prot
Levels & 2 = Add V View 1 X
Comments: 3 = Update A Add 2
4 = Delete U Update 3
D Delete 4 X
C Copy 3
R Review 1 X
W Withdraw txn 1 X
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit RStrt PrevS NextR Save
|
Screen two of the Application maintenance function is used to view or maintain security level and action information for NSM applications. If security levels are used, they must be entered in the Security Levels & Comments area in the format:
v = descriptionThe v denotes a one character security level value which must be followed by an equal sign. The actions must then be entered in list form accompanied by an action description, the minimum security level required by a user to perform that action (MSL) and a flag indicating whether the body of the screen should be protected from entry for that action (Prot).
The remaining sections address:
The following edits are performed on the input data for screen two. Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A,U |
All minimum security levels (MSL) specified in the action list must occur in the Security Levels & Comments area followed by an equal sign. |
|
Action |
Special Processing |
|
A,U |
The data base field VALID-SECURITY-LEVELS is constructed by concatenating all security level values parsed from the Security Levels & Comments area. This parsing is done by taking the first non-blank character from each line that contains an equal sign. |
The Menu maintenance figure is an example of the Menu maintenance function, or view an actual image of the Menu maintenance screen in a separate window.
Make changes and press ENTER to validate
NSOM 1 TEST Menu maintenance - M 01/15/01 11:43
Command: Action: U Desk: Appl: NSM-MS Cmd Sec Grp:
Val Sec Grp: Parm: Menu Cmd: MM
-------------------------------------------------------------------------------
Action: U Appl: NSM-MS Menu Cmd ID: MM Entered: Upd: 01/08/01
Menu Cmd Desc: nsm maintenance system Main Menu By: WDW
Cmd Description Required Keys T
LAAC List All Available Commands Command ID F
MHAC Menu Hierarchy of Available Commands F
DAM Desk Administrator's Menu M
ISM Initialization and Setup Menu M
AAM Application Administrator's Menu M
CDCD Change desk/Display Current Desk info U
LOG LOGon to another natural application U
FIN FINish your session (sign off natural) U
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit RStrt EdOpt NextR Save
|
The application Menu maintenance function is used to add, view, update, delete or copy information about the Natural Application's menus. The permitted Action codes are: A, V, U, D, or C respectively. Values for Appl ID, Menu Cmd ID, and Action are always required.
To add or update a menu command for an Appl ID, enter or replace valid values for the required fields. To view or delete, only the desired Application ID and Menu Command are necessary. To copy menu information from a record to either a new menu or an existing one, first display a source menu (a menu from which values will be copied). Next enter 'C' in the Action field and the Application ID and Menu Command ID to which values will be copied and press ENTER. PF10 is required to confirm and effect any change.
The remaining sections address:
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A,C |
Appl ID must exist as APPLICATION-ID on the APPLICATION file. |
|
A |
Appl ID and Menu Cmd ID must not exist as APPLICATION-ID and MENU-COMMAND-ID on the MENU-COMMAND file. |
|
A |
Menu Cmd ID must not exist as a function on another menu within the Application. |
|
V,U,D |
Appl ID and Menu Cmd ID must exist as APPLICATION-ID and MENU-COMMAND-ID on the MENU-COMMAND file. |
|
A,U,C |
Menu Cmd ID Description is required. |
|
A,U,C |
At least two Cmds are required per menu. |
|
A,U,C |
Cmds must be unique and may not appear on multiple menus. |
|
A,U,C |
T (Command Type) must be 'M', 'F' or 'U'. |
|
A,U,C |
Cmd must already exist as a menu if T is 'M' and must not exist as a menu if T is 'F' or 'U'. |
|
A,U,C |
Command Description is required for function modules (command types F or U). If T is 'M', MENU-COMMAND-DESCRIPTION is retrieved from the MENU-COMMAND file via Appl Id and Menu Cmd Id and displayed in the Description field. |
|
D |
A Menu Cmd ID may not be deleted if it exists as a COMMAND-ID within Appl ID on the MENU-COMMANDS file. |
|
A,U,C |
A Cmd may not be the same as the MENU-COMMAND it resides on. |
|
Action |
Special Processing |
|
A,U,C |
Menu Cmd ID description, Description, and Required Keys fields are not translated to upper case on input. |
|
Action |
Effect on Data Base |
|
A |
A new record is stored on the MENU-COMMAND file with the corresponding logical field assignments. Additional assignments include: DATE-OF-ENTRY and DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
U |
All the values for Cmd, Description, Required Keys, T, and Menu Cmd Id description are updated for the existing record on MENU-COMMAND. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
D |
The existing record for the Appl ID and Menu Cmd ID are deleted. |
|
C |
If the Menu Cmd ID already exists for the Appl ID, the effective action of the Copy is an Update. If the Menu Cmd ID does not exist, the effective action is an Add. Data base changes are as noted above for the respective effective action. |
The following sections document the List Applications of an Analyst function:
The List Applications of an Analyst figure is an example of the List Applications of an Analyst function, or view an actual image of the LAA screen in a separate window.
Figure: List
Applications of an Analyst screen
Select an entry, press PF8 to page forward, or enter new keys
NSOLAA 1 List Applications of an Analyst - LAA 01/12/94 09:23
Command: Action: U Desk: Appl: BIS Cmd Sec Grp:
Val Sec Grp: Parm: User: WDW End Appl: 99999999
-------------------------------------------------------------------------------
List for User: WDW Wimberly, W. David
starting from Appl: BIS thru Appl: 99999999
Application ID Application Name
_ BIS Balance Inquiry System
_ BOQSS Batch Oasis Query Submission Sys
_ BUDGET UAF Budget System
_ CS-ACCT Computing Services Accounting
_ DA-GRADS Dev & Alumni - Gift Recording & Dues Sys
_ DA-JOBS Batch job library for DA-GRADS
_ DA-RPTS Dev/Alumni Report Library
_ DHYATT David Hyatt's Library
_ DW85047 David Wimberly's library
_ GJIM General Journal Interface Module
Applications 1 thru 10 of 32 are displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt Forwd
|
The List Applications of an Analyst function is used to display applications for which a given user is an analyst. These applications are listed in sets of ten and include the application ID and name. Use PF8 to scroll forward through the list of applications. The display near the bottom of the screen indicates which set of applications is displayed and the total number of applications. PF5 will restart the list with the first set of applications. Application IDs may be marked for selection and further processing.
Users are defined as analysts of an application through the Application maintenance (A) function.
| User ID | Identifies the user for which the list of applications is to be generated. A list of User IDs by user name can be obtained by pressing PF1 (Help) while the cursor is on this field. This list is in sequence of the name of the individual assigned to the ID. |
| Application ID | Application ID is used as a starting search value for the list. |
| Ending Application ID | Identifies the ending value for the list of applications. This field defaults to high values, but may be changed by the user. |
PF4 is used to decode selected entries. To obtain additional information about the application, mark the desired application and press PF4. The application's total number of desks, command security groups, and value security groups and the date of the last notice for the application are displayed in a window.
| A | Application maintenance is used to set up an application and define its owners and analysts. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
This menu contains the functions used by application administrators to grant access to applications, post notices for users of applications, temporarily restrict access to applications or to review these definitions in effect. The complete menu appears in Application Administrator Menu figure, or view an actual image of the AAM screen in a separate window.
Figure: Application
Administrator Menu
Enter, mark or position cursor to desired command
NSOMENU 1 Application Administrator Menu - AAM 01/11/94 10:28
Command: Action: V Desk: Appl: Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
CMD Command description Required key fields
---- ---------------------------------------- ------------------------------
_ CS Command Security group maintenance Appl & Cmd Sec Grp
_ VS Value Security group maintenance Appl & Val Sec Grp
_ AD Application-Desk maintenance Desk & Appl
_ ADA Application Default Access Appl
_ AN Application Notice maintenance Appl
_ ALR Application Lock/unlock & Reason Appl
_ CSLR Cmd Security group Lock/unlock & Reason Appl & Cmd Sec Grp
_ LUA List Users of an Application Appl & User
_ LDC List Desks for a Command security group Appl & Cmd Sec Grp
_ LDV List Desks for a Value security group Appl & Val Sec Grp
_ LDA List Desks for an Application Desk & Appl
_ LAO List Applications of an Owner Desk Desk & Appl
_ CSQ Command SeQuence list maintenance Appl & Cmd Seq Name
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Quit
|
The Command Security figure is an example of the Command Security group maintenance function, or view an actual image of the Command Security group maintenance screen in a separate window.
Figure: Command
Security group maintenance
Make changes and press ENTER to validate
NSOCS 1 TEST Command Security group maintenance - CS 10/23/96 12:05
Command: Action: U Desk: Appl: NSM-MS Cmd Sec Grp: SPEC
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
Action: U Application Id: NSM-MS Natural Secured Menus - Maintenance Sys
Cmd Sec Grp: SPEC Desc: Test of the S -- as Specified -- Cmd A/D/S
Commands Allowed, Disallowed, or as Specified (A,D or S): S
Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL Cmd SL
------ ------ ------ ------ ------ ------ ------ ------ ------ ------
D -
UD -
LUD -
U 2
ADA 2
CS
AD
Entered: 10/22/96 Updated: 10/23/96 By: WDW
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt ShowC NextR Save
|
The application Command Security maintenance function is used to add, view, update, delete, or copy information about Natural Applications' Command Security Groups. The permitted Action codes are: A, V, U, D, or C respectively. Values for Application ID, Command Security Group, and Action are always required.
To add or update a Command Security Group, enter or replace valid values for the required fields. To view or delete, only the desired Application ID and Command Security Group are necessary. To copy command security group information to either a new command security group or an existing group, first view the source command security group (or enter values on the screen to be copied). Then enter 'C' in the Action field and the destination Command Security Group to which the screen values are to be copied and press ENTER. PF10 is required to confirm and effect any change.
The remaining sections address:
Command security is designed to provide the greatest flexibility possible to the application administrator while requiring a minimum of effort. This is accomplished by providing three options for defining command restrictions, which is indicated by the value entered into the Commands Allowed, Disallowed, or as Specified field.
|
A |
An A indicates that the list of commands provided will be an inclusive list of all commands allowed. Any command not listed will not be available to users (desks) assigned this command security group. Further, a Security Level may be specified for selected commands. If provided (non-blank), that security level will be assigned to the user within that function if that level is less than the user's (desk's) normal security level. |
|
D |
D indicates that the list of commands provided are to be disallowed for the user. The user will be permitted access to all commands other than those listed, always with the user's normal security level. |
|
S |
S indicates that access to commands is provided as specified or with view only access when not specified. Any command not listed will be accessible by the user but with the most restrictive security level available within the application (normally this would be View only). Three additional options are available for those commands listed based upon the associated Security Level specification:
|
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A |
Appl (Application ID) and Cmd Sec Grp (Command Security Group) must not exist on the COMMAND-SECURITY file. |
|
A,C |
Appl (Application ID) must exist on the APPLICATION file. |
|
V,U,D |
Appl (Application ID) and Cmd Sec Grp (Command Security Group) must exist on the COMMAND-SECURITY file. |
|
A,U,D |
The desk ID of the operator must be an Application-Owner-Desk-ID on the APPLICATION file for this Application ID. |
|
A,U.C |
Desc (Command Security Group Description) is required, it cannot be left blank. |
|
A,U,C |
Cmd (commands) must be unique, a command cannot be repeated within this list. |
|
A,U,C |
Cmd (commands) must exist as valid Command-IDs on the MENU-COMMAND file for this Application Id. |
|
A,U,C |
Commands Allowed, Disallowed, or as Specified (A,D or S) is a required field and must be an A, D or S. On an Add, it is initialized to 'D'. If the action requested is a Copy, this field's value is copied from the source. The value S is only permitted for NSM version 2 applications (BASIS applications or any others generated using the UAF Program Generator). |
|
A,U,C |
SL (security level) can only be entered if Commands Allowed, Disallowed, or as Specified is an A or S. This value must be a valid security level for the application, as defined on screen 2 of the Application maintenance function (command A). Further, if Commands Allowed, Disallowed, or as Specified is S, this value may be an '-' indicating that this command is not allowed. See "Command Allowed, Disallowed, or as Specified" for additional information. |
|
A,U,C |
The Main-Menu-Command-ID for the application must be allowed or not disallowed. |
|
D |
A Command Security Group may not be deleted if any desk provided access to the application on the APPLICATION-DESK file (via command AD) has this same value. |
|
Action |
Special Processing |
|
A,U,C |
Cmd Sec Grp Desc is not translated to upper case on input. |
|
A,U,C |
PF6 is labeled as ShowC for show commands. When pressed, all commands defined for the application are retrieved and placed in the list of commands available on the screen. If modifications have been made on the screen and not saved, a warning message is displayed when PF6 is pressed that notifies the user that commands previously listed and any associated security levels are erased. Selected commands can then be blanked out as necessary. This function is useful when an application contains a large a number of commands that might be difficult to remember and enter. |
|
V,U |
When PF4 is pressed, the name of the user to last update the Command Security Group is retrieved from the USER file and displayed. |
Data base changes are only performed if all data is valid and PF10 is entered.
|
Action |
Effect on Data Base |
|
A |
A new record is stored on the COMMAND-SECURITY file with the corresponding field assignments. Additional assignments include: COMMAND-GROUP-LOCK = U, DATE-OF-ENTRY and DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
U |
The existing record on the COMMAND-SECURITY file is updated with the corresponding field assignments. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
D |
The existing record on the COMMAND-SECURITY file is deleted. |
|
C |
If the Command Security Group exists for the Application ID, the effective action of the Copy is an Update. If the Command Security Group does not exist, the effective action is an Add. Data base changes are as noted above for the respective effective action. |
The Value Security maintenance figure is an example of the Value Security group maintenance function, or view an actual image of the Value Security maintenance screen in a separate window.
Figure: Value
Security group maintenance
Please enter new key fields NSOVS 1 Value Security group maintenance - VS 08/30/93 09:37 Command: Action: V Desk: Appl: NSM-MS Cmd Sec Grp: DM-ONLY Val Sec Grp: AVCF Parm: ------------------------------------------------------------------------------- Action: V Appl: NSM-MS Val Sec Grp: AVCF +-----------------------------------------------------------------------------+ | Press ENTER or PF3 to specify new keys | | | | Group description: Financial Affairs | | | | Permit unrestricted access (Y/N): N | | | | Restrict access to budgetary unit(s): | | AVCF ASSO VICE CHAN FIN | | | | | | | | | | Last updated: 08/19/93 By: WDW | | | | Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11-- | | Quit N 3 V | +-----------------------------------------------------------------------------+ |
The Value Security maintenance function is used to add, view, update, or delete information about NSM applications' Value Security Groups on the VALUE-SECURITY file. The permitted Action codes are: A, V, U, or D respectively. Values for Application ID, Value Security Group, and Action are always required.
To add or update a Value Security Group, enter or replace valid values for the required fields. To view or delete, only the desired Application ID and Value Security Group are necessary. PF10 is required to confirm and effect any change.
Since value security requirements differ for all applications, value security maintenance is performed within a window which fills the main body of the screen. This window is presented and processed by different subprograms for each application. Because a subprogram handles the user inputs, the main program does not issue the standard warning when data is modified and the user's action will result in loss of those changes. Each subprogram must be customized for an application so that the fields needed by the application to apply record level restrictions can be defined. NSM accesses these restrictions at the time of user signon and passes this information to the function modules so that they can restrict access as necessary.
The remaining sections address:
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A |
Application ID and Value Security Group must not exist on the VALUE-SECURITY file. |
|
A |
Application ID must exist on the APPLICATION file |
|
V,U,D |
Application ID and Value Security Group must exist on the VALUE-SECURITY file. |
|
A,U,D |
The desk of the operator must be an APPLICATION-OWNER-DESK-ID on the APPLICATION file for this Application ID. |
|
A,U |
Group description is required. |
|
A,U |
The fields used to define value based security for an application may have specific edit requirements which are enforced. The error messages displayed for these fields and help information available should adequately describe the necessary inputs. |
|
D |
A Value Security Group may not be deleted if any APPLICATION-DESK on the APPLICATION-DESK file has this same value in their VALUE-SECURITY-GROUP field. |
|
Action |
Special Processing |
|
A,U |
Group description is not translated to upper case on input. |
Data base changes are only performed if all data is valid and PF10 is pressed.
|
Action |
Effect on Data Base |
|
A |
A new record is stored on the VALUE-SECURITY file with the corresponding logical field assignments. Additional assignments include: DATE-OF-ENTRY and DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
U |
The existing record on the VALUE-SECURITY file is updated with the corresponding logical field assignments. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
|
D |
The existing record on the VALUE-SECURITY file is deleted. |
The following sections document assignment of Desks to Applications.
The Application Desk maintenance figure is an example of the Application Desk maintenance function, or view an actual image of the AD screen in a separate window.
Figure: Application
Desk maintenance
Press PF8 to view more records or enter new keys
NSOAD 1 TEST Application-Desk maintenance - AD 01/15/01 14:29
Command: Action: V Desk: Appl: LEAVE Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
Action: V Appl: LEAVE Leave Accounting
Desk:
Sec Job Command Value
Desk Id Name Lvl Sec Class Sec Group Sec Group
ACHERON Converted for Eric Robinson 9 USERTEST ER
ADMETUS Converted for Cathy Renner 9 USERTEST CR
AETHER Converted for Lisa Danley 7 DEPTREP COMP
APPLE Desk for Wilma Carr 9 USERTEST WC
ARACHNE Programmer on Basis 9 A ALL COMP
ARES Converted for Allen Fields 9 A ALL COMP
ARGUS Duchess of Time Travel 9 A ALL COMP
ASH Desk for GLTST06 9 DEPTREP LVADMIN
ASTRAEA Converted for Lonnie Deavens 9 ALL COMP
ATLAS Don Barnett 9 ALL COMP
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode Forwd
|
The Application Desk maintenance function is used to maintain the assignments of desks to Natural Secured Menus (NSM) applications. An assignment of a desk to an application consists of granting access and establishing security for that desk within the application. This screen has been designed so that more than one record may be updated at one time. A maximum of ten desks are displayed on a screen.
| Action | Possible values for action include V (View), A (Add), U (Update), and D (Delete). Only an owner of the Application may Add, Update, or Delete Application-Desk assignments. See "Actions" for descriptions of these types of processing. |
| Application ID | A list of valid Application IDs may be obtained by pressing PF1 (Help) while the cursor is positioned on this field. |
| Desk ID | Desk ID is required to Add or Delete a specific assignment of the Desk to the Application. To View or Update, Desk ID is used as a starting value so that up to ten records may be viewed or updated at one time. A list of Desk IDs by user name may be obtained by pressing PF1 (Help) while the cursor is positioned on this field. |
The following actions are possible for this function. Use of some actions may be restricted for some users. No data will be created, modified, or deleted until PF10 is pressed.
To view Application-Desk assignments, enter in the banner a 'V' in the Action field and a valid Application ID. If desired, a starting value for Desk ID may be entered. All Application-Desk records found after that starting value for the specified Application will be displayed. PF8 may be used to scroll forward to view the remaining Desks assigned to that Application.
To assign a Desk to an Application, enter in the banner an 'A' in the Action field, the Desk ID, and the Application ID. Only one Desk assignment can be created at a time. The first line of the list will contain the Desk ID that is being assigned access to the specified Application. This will be the only line where data entry is permitted. If there are Desks assigned to the Application that fall alphabetically after the new Desk ID, they will be listed but will be protected from entry. Enter the desired values for the remaining fields. Job Security Class and Value Security Group are only required if the Application uses these types of security.
To update existing Application-Desk assignments, enter in the banner a 'U' in the Action field and the Application ID for which desk assignments have been made. If desired, a starting value for Desk ID may also be entered. Up to ten Desk IDs will be displayed, beginning with the Desk ID entered in the banner, and all those listed may be modified. PF8 may be used to scroll through records on an Update, but PF10 must be pressed prior to pressing PF8 to save any changes made to the Application-Desk records displayed.
To delete an existing Application-Desk assignment, enter in the banner a 'D' in the Action field, the required Application ID, and Desk ID. As with Add, only one Application-Desk assignment can be deleted at a time.
To see additional information about the Application-Desk assignment, position the cursor anywhere on the line of the desired entry and press PF4. A window will display the date of entry, date of last update, and the Natural ID of the user who last updated the Application-Desk assignment. Additionally, descriptions for the command security group and value security group will be shown.
| Desk Definition | A definition of the virtual concept of a desk used to define a job function or administrative role. |
| Desk Function | A description of how desks are used to control application access and for electronic transaction routing and approval. |
| LDB | List Desks by Budgetary unit. |
| LDC | List Desks for a Command security group. |
| LDV | List Desks for a Value security group. |
| LUD | List Users assigned to a Desk. |
| LAD | List Applications to which a Desk has access. |
The following sections document the Application Default Access function:
The Application Default Access figure is an example of the Application Default Access maintenance function, or view an actual image of the ADA screen in a separate window.
Figure: Application
Default Access maintenance
All entries are valid, press PF10 to Save
NSOADA 1 Application Default Access - ADA 08/30/93 09:40
Command: Action: U Desk: Appl: BIS Cmd Sec Grp: DM-ONLY
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
Action: U Appl: BIS Balance Inquiry System
Default Access Permitted? (Y/N) Y
Default Security Level: 5
Default Command Security Group: NORM
Command security for normal users
Default Value Security Group: NO04
No 04 companies
Entered: Updated: 03/04/93 By: EORWIG
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt NextR Save
|
The Application Default Access function is used to establish or eliminate default access for an application. Only an application owner can determine if the application can have default access and assign the security definitions for that access. If an application has been defined by this function as allowing default access, then any user may logon to the application. The user's security and the accessible commands are based upon the assignments defined in this function.
| Action | Possible values for action are V (View) and U (Update). See "Actions" for descriptions of these types of processing. |
| Application ID | A list of valid Application IDs may be obtained by pressing PF1 (Help) while the cursor is positioned on this field. |
The following actions are possible for this function. Use of the Update action may be restricted for some users. No data will be modified until PF10 is pressed.
To view information about an application's default access availability and default security definitions, enter in the banner a 'V' in the Action field and the desired Application ID.
To modify an application's default access availability and default security definitions, enter in the banner a 'U' in the Action field and the desired Application ID. To allow default access for the application, enter 'Y' in the Default Access Permitted field. A security level and command security group are required so that default security can be properly defined. If the application uses security by value, a default value security group is also required. To eliminate default access for the application, enter an 'N' in the Default Access Permitted field. The remaining fields that assign default security definitions will be reset to blank because they are not needed if default access is not permitted.
PF4 (DCode) can be used to display the names of the command security and value security groups that have been defined for default access.
| CS | Command Security group maintenance is used to create, modify, and delete command security groups for an application. |
| VS | Value Security group maintenance is used to create, modify, and delete value security groups for an application. |
The Application Notice maintenance figure is an example of the Application Notice maintenance function, or view an actual image of the AN screen in a separate window.
Figure: Application
Notice maintenance
Please enter new key fields
NSOAN 1 Application Notice maintenance - AN 08/30/93 09:42
Command: Action: V Desk: Appl: DA-GRADS Cmd Sec Grp:
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
Action: V Appl: DA-GRADS Dev & Alumni - Gift Recording & D Eff Date: 01/19/1990
*
*
* The DA-GRADS application is now in production. You have accessed
* the TEST system. To access production, enter CICSPROD from the
* VMVTAM menu. The test system is available for testing.
*
*
Entered: Last Updated: 08/17/93 By: WDW
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode NextR
|
The Application Notice maintenance function is used to add, view, update, delete, or copy a Notice associated with a specific existing Natural Application on the APPLICATION file. This notice will be automatically displayed to any user when they logon to the application if their DATE-LAST-LOGGED-ON on the APPLICATION-USER file is before the DATE-NOTICE on the APPLICATION.
The permitted Action codes are: A, V, U, D, or C respectively. Values for Application ID and Action are always required.
To add or update, enter or replace valid values for the required fields. To view or delete, only the desired Application ID is necessary. To copy a notice to another application, display the source application's notice and enter 'C' in the Action field and the Application ID to which the notice is to be copied. The effective action of a Copy is always an Update. PF10 is required to confirm and effect any change.
The remaining sections address:
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
A,V,U,D,C |
Appl ID must exist on the APPLICATION file |
|
A,U,C |
The notice text must be non-blank. |
|
A,U,C |
Eff Date (Effective Date) must be greater than or equal to the current system date. |
|
A,U,D,C |
Only an owner whose desk is one of the APPLICATION-OWNER-DESK-IDs or an analyst whose user ID is an APPLICATION-ANALYST on the APPLICATION file for this Application ID may update/delete the notice Eff Date or text. |
|
Action |
Special Processing |
|
A,U,C |
Notice text is not translated to upper case on input. |
|
V,U,C,D |
When PF4 is pressed, the name of Last Updated By (UPDATED-BY-USER) is retrieved from the USER file and displayed. |
|
Action |
Effect on Data Base |
|
A,U,C |
The DATE-NOTICE and the NOTICE fields on the APPLICATION file for the Application ID entered are updated with the contents of Eff Date and the notice text. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID, and DATE-OF-ENTRY = current date (for an Add). |
|
D |
The existing values for DATE-NOTICE and NOTICE on the APPLICATION file are updated with blanks and zeros respectively. Additional assignments include: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
The Application Lock/unlock Reason figure is an example of the Application Lock/unlock and Reason maintenance function, or view an actual image of the ALR screen in a separate window.
Figure: Application
Lock/unlock and Reason
All entries are valid, press PF10 to Save
NSOALR 1 Application Lock/unlock & Reason - ALR 08/30/93 09:43
Command: Action: U Desk: Appl: DA-GRADS Cmd Sec Grp:
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
Action: U Appl: DA-GRADS Dev & Alumni - Gift Recording & Dues Sys
Lock/Unlock: L
Reason for locking the application:
Sample explanation of why an application may
be locked up and when it will again become
available.
Entered: Last Updated: 08/17/93
By: WDW
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt NextR Save
|
To update, replace the desired fields with valid values. To view, only the desired Application ID is necessary. PF10 is required to confirm and effect any change.
The remaining sections address:
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
V,U |
Application ID must exist on the APPLICATION file. |
|
U |
The desk of the operator must be a valid APPLICATION-OWNER-DESK-ID or the operator's user ID must be an APPLICATION-ANALYST on the APPLICATION file for this Application ID. |
|
U |
If Lock/unlock is 'L', the Reason for locking the application cannot be blank. |
|
U |
If Lock/unlock is 'U' the REASON-APPLICATION-LOCKED will be blanked on update to the APPLICATION file for the Application ID. |
|
Action |
Special Processing |
|
U |
The Reason for locking the application text is not translated to upper case on input. |
|
V,U |
When PF4 is pressed, the name of Last Updated By (UPDATED-BY-USER) is retrieved from the USER file and displayed. |
Data base changes are only performed if all data is valid and PF10 is entered.
|
Action |
Effect on Data Base |
|
U |
If Lock/unlock is 'L' the APPLICATION-LOCKED and REASON-APPLICATION-LOCKED fields are updated on the APPLICATION file with Lock/unlock and 'Reason' text for the Application ID. If Lock/unlock is 'U' the APPLICATION-LOCKED field is updated with 'U' and the REASON-APPLICATION-LOCKED field is updated with blanks on the APPLICATION file for the Application ID. The corresponding logical field are always updated DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
The Command Security group Lock/unlock and Reason figure is an example of the Command Security group Lock/unlock and Reason function, or view an actual image of the CSLR screen in a separate window.
Figure: Command
Security group Lock/unlock and Reason
Specified key does not exist; make changes and press ENTER to validate
NSOCSLR 1 Cmd Security group Lock/unlock & Reason - CSLR 08/30/93 09:44
Command: Action: U Desk: Appl: DA-GRADS Cmd Sec Grp:
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
Action: U Appl: DA-GRADS Dev & Alumni - Gift Recording & Dues Sys
Cmd-Sec-Grp Lock/Unlock Cmd-Sec-Grp Lock/Unlock
ALL U
ALLTBL U
NOMAD l
Reason Command Security Groups Locked:
Sample of locking one command security group
out of an application.
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit RStrt UnLok Save
|
The Command Security group Lock/unlock and Reason function is used to view or update information about Natural Applications' Command Security Groups lock/unlock status and reason for the lock. This information is contained on the COMMAND-SECURITY file and APPLICATION file respectively for an Application ID. The permitted Action codes are: V or U, respectively. A value for Application ID is always required.
To update, replace the desired fields with valid values. To view, only the desired Application ID is necessary. A maximum of 10 Cmd Sec Grps are displayed on a screen, and PF8 can be used to scroll through the Cmd Sec Grps for the specified Application Id. PF10 is required to confirm and effect any change.
The remaining sections address:
Invalid entries will result in an error and must be corrected before any data base change is allowed.
|
Action |
Validation |
|
V,U |
Application ID must exist on the COMMAND-SECURITY file. |
|
V,U |
Cmd Sec Grp, if entered in the command-key area and if it exists on the COMMAND-SECURITY file for this Application ID, will be the first of the ten Cmd Sec Grps listed to be locked or Unlocked. If the Cmd Sec Grp entered does not exist, the first ten existing COMMAND-SECURITY-GROUPS within the Application ID after the specified Cmd Sec Grp will be listed. |
|
V,U |
At least one COMMAND-SECURITY-GROUP must exist for this Application Id on the COMMAND-SECURITY file. |
|
U |
The desk of the operator must be an APPLICATION-OWNER-DESK-ID on the APPLICATION file for this Application. |
|
U |
Lock/Unlock is a required field and must be L or U for all listed Cmd Sec Grps. |
|
U |
Reason Command Security Groups Locked text is required. |
|
Action |
Special Processing |
|
U |
Reason Command Security Groups Locked text is not translated to upper case on input. |
|
U |
When PF6 is pressed, all the Cmd Sec Grps will be assigned an Unlock status. |
|
U,V |
Cmd Sec Grps will be displayed in groups of ten starting with the first COMMAND-SECURITY-GROUP within the Application ID or the Cmd Sec Grp entered. Pressing PF8 will page forward through the Cmd Sec Grps. |
Data base changes are only performed if all data is valid and PF10 is entered.
|
Action |
Effect on Data Base |
|
U |
The existing records on the COMMAND-SECURITY file for the Application Id and Cmd Sec Grps are updated with the corresponding COMMAND-GROUP-LOCK = Lock/Unlock. The existing record on the APPLICATION file for the Application ID is updated with REASON-CSG-LOCKED = Reason Command Security Groups Locked text. The COMMAND-SECURITY file is updated with the corresponding logical field assignments: DATE-LAST-UPDATED = current date and LAST-UPDATED-BY = current Natural user ID. |
The following sections document the List Users of an Application function:
The List Users of an Application figure is an example of the List Users of an Application function, or view an actual image of the LUA screen in a separate window.
Figure: List Users
of an Application
Select an entry, press PF8 to page forward, or enter new keys
NSOLUA 1 List Users of an Application - LUA 08/30/93 09:45
Command: Action: U Desk: Appl: GJIM Cmd Sec Grp:
Val Sec Grp: AVCF Parm: User:
-------------------------------------------------------------------------------
List for Appl: GJIM starting from
User LastLogon Name BUNIT
_ AP001 Lester, Tina AVCF
_ AP04 Omohundro, Doris AVCF
_ AVCF001 08/19/93 Briney, Colleen AVCF
_ AVCF002 05/21/93 Danley, Lisa AVCF
_ AVCF01 06/29/93 Stolfi, Larrie AVCF
_ AVCF02 08/18/93 Bronaugh, Jim AVCF
_ AVCF07 08/13/93 Shaw, Phyllis AVCF
_ BKENNED 07/28/93 Kennedy, Bobbie AVCF
_ BMOODY Moody, Bill CAUD
_ BROMLEY 08/12/93 Bromley, Katrina COMP
Users 1 thru 10 displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt Forwd
|
The List Users of an Application function is used to display users of an application, anyone that has ever logged onto the application. These users are listed in sets of ten and include the user ID and the date of the last logon to the application. Use PF8 to scroll forward through the list of users. The display near the bottom of the screen indicates which set of users is displayed and the total number of users. PF5 will restart the list with the first set of users. User IDs may be marked for selection and further processing.
Users are created through the User maintenance (U) function.
| Application ID | Identifies the application for which the list is generated. A list of valid application IDs may be obtained by pressing PF1 (Help) while the cursor is on this field. |
| User ID | User ID is used as a starting search value such that all users with an ID equal to or greater than that value are listed. A blank ID will obtain a complete list of the users of the application. A list of assigned User IDs displayed in user name order may be obtained by pressing PF1 (Help) while the cursor is on this field. |
PF4 is used to decode all entries in the list. To obtain the user name and the budgetary unit to which the ID is assigned, press PF4.
| U | User maintenance is used to define and modify user IDs. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
The following sections document the List Desks for an Command security group function:
The List Desks for a Command security group figure is an example of the List Desks for a Command security group function, or view an actual image of the LDC screen in a separate window.
Figure: List Desks
for a Command security group
Select an entry, press PF8 to page forward, or enter new keys
Desk name and BUNIT decoded LDC 07/28/94 10:16
Command: Action: V Desk: Appl: LEAVE Cmd Sec Grp: ALL
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
Appl: LEAVE Cmd Sec Grp: ALL Allow access to all commands
Sec Value
Desk Lvl Sec Grp Desk Name BU
_ ARGUS 9 COMP Converted for Katrina Bromley COMP
_ AUSTER 9 LVADMIN Converted for Joy Steely COMP
_ CHAOS 9 COMP Converted for W. David Wimberly COMP
_ AVERNUS 9 COMP Converted for Kathryn Cantrell COMP
_ ATLAS 9 COMP Don Barnett COMP
_ COCYTHUS 9 LVADMIN Converted for Bill Overby HMRS
_ BRIAREUS 9 COMP Converted for Paul Bixby COMP
_ CEPHALUS 9 COMP Converted for Sandra Twiggs COMP
_ ARACHNE 9 COMP Converted for Ava Findahl COMP
_ FSTC 9 LVADMIN Financial Systems Training Coordinator AVCF
Desks 1 thru 10 of 12 displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt Forwd
|
The List Desks for a Command security group function is used to display desks with a given command security group for the specified application. These desks are listed in sets of ten and include the desk ID, security level, and value security group. Use PF8 to scroll forward through the list of desks. The display near the bottom of the screen indicates which set of desks is displayed and the total number of desks. PF5 will restart the list with the first set of desks. Desk IDs may be marked for selection and further processing.
Desks are granted access to applications through the Application-Desk (AD) function.
| Application ID | Identifies the application for which the list is generated. A list of valid application IDs may be obtained by pressing PF1 (Help) while the cursor is on this field. |
| Command Security Group | Identifies the command security group of the specified application for which the list is generated. |
PF4 is used to decode all entries in the list. To obtain the desk name and the budgetary unit associated with the desk, press PF4.
| Desk Definition | A definition of the virtual concept of a desk used to define a job function or administrative role. |
| Desk Function | A description of how desks are used to control application access and for electronic transaction routing and approval. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
| AD | Application Desk maintenance is used to grant access to an application. |
| CS | Command Security maintenance is used to define command security groups for an application. |
| LAD | List Applications to which a Desk has access. |
| LUD | List Users assigned to a Desk. |
The following sections document the List Desks for an Value security group function:
The List Desks for a Value security group figure is an example of the List Desks for a Value security group function, or view an actual image of the LDV screen in a separate window.
Figure: List Desks
for a Value security group
Select an entry or enter new keys
NSOLDV 1 List Desks for a Value security group - LDV 08/30/93 09:47
Command: Action: U Desk: Appl: NSM-MS Cmd Sec Grp: CORETEAM
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
Appl: NSM-MS Val Sec Grp: AVCF Financial Affairs
Sec Cmd
Desk Lvl Sec Grp Desk Name BUNIT
_ FSTC 7 AA+DM Financial Systems Training Coordinator AVCF
Desks 1 thru 1 of 1 displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt
|
The List Desks for a Value security group function is used to display desks with a given value security group for the specified application. These desks are listed in sets of ten and include the desk ID, security level, and command security group. Use PF8 to scroll forward through the list of desks. The display near the bottom of the screen indicates which set of desks is displayed and the total number of desks. PF5 will restart the list with the first set of desks. Desk IDs may be marked for selection and further processing.
Desks are granted access to applications through the Application-Desk (AD) function.
| Application ID | Identifies the application for which the list is generated. A list of valid application IDs may be obtained by pressing PF1 (Help) while the cursor is on this field. |
| Value Security Group | Identifies the value security group of the specified application for which the list is generated. |
PF4 is used to decode all entries in the list. To obtain the desk name and the budgetary unit associated with the desk, press PF4.
| Desk Definition | A definition of the virtual concept of a desk used to define a job function or administrative role. |
| Desk Function | A description of how desks are used to control application access and for electronic transaction routing and approval. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
| AD | Application Desk maintenance is used to grant access to an application. |
| VS | Value Security maintenance is used to define value security groups for an application. |
| LAD | List Applications to which a Desk has access. |
| LUD | List Users assigned to a Desk. |
The following sections document the List Desks for an Application function:
The List Desks for an Application figure is an example of the List Desks for an Application function, or view an actual image of the LDA screen in a separate window.
Figure: List Desks
for an Application
Select an entry, press PF8 to page forward, or enter new keys
NSOLDA 1 List Desks for an Application - LDA 08/30/93 09:48
Command: Action: U Desk: Appl: GJIM Cmd Sec Grp: CORETEAM
Val Sec Grp: AVCF Parm:
-------------------------------------------------------------------------------
List for Appl: GJIM starting from
Sec Value Cmd
Desk ID Lvl Sec Grp Sec Grp Desk Name BUNIT
_ ADONIS 6 CORETEAM Converted for Craig A. Brown AVCB
_ AEACUS 6 CORETEAM Converted for Donna Carter AVCB
_ AEETES 6 CORETEAM Converted for Daniel Jones AVCB
_ AEGEUS 6 CORETEAM Converted for William Rains AVCB
_ AEGYPTUS 6 CORETEAM Converted for Tina Lester AVCF
_ AEOLUS 6 CORETEAM Converted for Doris Omohundro AVCF
_ AESON 6 CORETEAM Converted for Colleen Briney AVCF
_ AETHER 6 CORETEAM Converted for Lisa Danley AVCF
_ AGIAIA 6 CORETEAM Converted for Larrie Stolfi AVCF
_ AJAX 6 CORETEAM Converted for Jim Bronaugh AVCF
Desks 1 thru 10 displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt Forwd
|
The List Desks for an Application function is used to display desks that have been granted access to an application. These desks are listed in sets of ten and include the desk ID, desk name, and the desk's budgetary unit. Use PF8 to scroll forward through the list of desks. The display near the bottom of the screen indicates which set of desks is displayed and the total number of desks. PF5 will restart the list with the first set of desks. Desk IDs may be marked for selection and further processing.
Desks are granted access to applications through the Application-Desk (AD) function.
| Desk ID | Desk ID is used as a starting value. A list of assigned Desk IDs displayed in user name order may be obtained by pressing PF1 (Help) while the cursor is on this field. |
| Application ID | Identifies the application for which the list is generated. A list of valid application IDs may be obtained by pressing PF1 (Help) while the cursor is on this field. |
| Desk Definition | A definition of the virtual concept of a desk used to define a job function or administrative role. |
| Desk Function | A description of how desks are used to control application access and for electronic transaction routing and approval. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
| AD | Application Desk maintenance is used to grant access to an application. |
| LAD | List Applications to which a Desk has access. |
| LUD | List Users assigned to a Desk. |
The following sections document the List Applications of an Owner function:
The List Applications of an Owner figure is an example of the List Applications of an Owner function, or view an actual image of the LAO screen in a separate window.
Figure: List
Applications of an Owner
Select an entry, press PF8 to page forward, or enter new keys
NSOLAO 1 List Applications of an Owner desk - LAO 01/12/94 09:49
Command: Action: U Desk: CHAOS Appl: C Cmd Sec Grp:
Val Sec Grp: Parm:
-------------------------------------------------------------------------------
List for Desk: CHAOS Converted for W. David Wimberly
starting from Appl: C
Application ID Application Name
_ DA-GRADS Dev & Alumni - Gift Recording & Dues Sys
_ DA-JOBS Batch job library for DA-GRADS
_ DA-RPTS Dev/Alumni Report Library
_ DHYATT David Hyatt's Library
_ DW85047 David Wimberly's library
_ GJIM General Journal Interface Module
_ HRLY-TS Hourly Time Sheets
_ HRMS Human Resource Management System
_ INRS Institutional Research Application
_ JOBS Job Submission Application
Applications 1 thru 10 of 35 are displayed
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode RStrt Forwd
|
The List Applications of an Owner function is used to display applications for which a given desk is an owner. These applications are listed in sets of ten and include the application ID and name. Use PF8 to scroll forward through the list of applications. The display near the bottom of the screen indicates which set of applications is displayed and the total number of applications. PF5 will restart the list with the first set of applications. Application IDs may be marked for selection and further processing.
Desks are defined as owners of an application through the Application maintenance (A) function.
| Desk ID | Identifies the desk for which the list of applications is to be generated. A list of Desk IDs by user name can be obtained by pressing PF1 (Help) while the cursor is on this field. This list is in sequence of the name of the individual assigned to the desk. |
| Application ID | Application ID is used as a starting search value for the list. |
PF4 is used to decode selected entries. To obtain additional information about the application, mark the desired application and press PF4. The application's total number of desks, command security groups, and value security groups and the date of the last notice for the application are displayed in a window.
| A | Application maintenance is used to set up an application and define its owners and analysts. |
| LUD | List Users assigned to a Desk. |
| List Functions | Describes the features and characteristics of NSM list functions, such as standard PF Keys and how to select an entry for further processing. |
The following sections document the Command Sequence function:
The Command Sequence maintenance figure is an example of the Command SeQuence maintenance function, or view an actual image of the CSQ screen in a separate window.
Figure: Command
Sequence maintenance
Please enter new key fields
De-coding has been performed CSQ 07/28/94 14:43
Command: Action: V Desk: Appl: GJIM Cmd Sec Grp:
Val Sec Grp: Parm: Cmd Seq: TESTACT
-------------------------------------------------------------------------------
Action: V Appl: GJIM Command Sequence: TESTACT
Command Sequence Description: Testing the Action Field
Action Cmd Description
V JEM Journal Entry Maintenance
U JEM Journal Entry Maintenance
V JETP Journal Entry TARGET Processing
JEM Journal Entry Maintenance
Entries 1 thru 4 of 4 displayed; maximum allowed: 10
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Suspd Quit DCode NextR
|
The Command SeQuence maintenance function is used to create and maintain a series of two or more commands that are used in conjunction with each other to accomplish a particular task. Multiple command sequences are allowed within an application and the commands in those sequences are performed via the List Command SeQuence (LCSQ) function that exists in each application. Normally all commands in a sequence operate on the same banner key (or group of keys). The objective of this function is to prevent repetitive command entry for each new key entered in the banner.
An example of how this function might be used is when data for a particular entity (e.g. Personnel ID, Vendor Number, etc.) is to be maintained and there are multiple functions required to access all of the fields. The entity's banner key is entered one time and then LCSQ is used to access all of the required commands with the indicated action (in the order listed). Upon return to the list a new key is entered in the banner and the sequential execution of commands is repeated. Note that because the commands are sequential executed in LCSQ, it is important that are listed in the order in which they are to be executed.
| Action | Possible values for action include V (View), A (Add), U (Update) and D (Delete). See topic "Actions" for descriptions of these types of processing. |
| Appl | A list of Application IDs can be obtained by pressing PF1 (Help) while the cursor is positioned on this field. This list is in alphabetical order. |
| Cmd Seq | The Command Sequence Name is a unique name given to each command sequence within an application. |
The following actions are possible for this function. Use of some actions may be restricted for some users. No data will be created, modified, or deleted until PF10 is pressed.
To view an existing command list, enter in the banner a 'V' in the Action field and the desired Application ID and Command Sequence Name.
To create a new command sequence, enter in the banner an 'A' in the Action field, the desired Application ID, and the new Command Sequence Name. Enter the command sequence Description and valid Command IDs.
To modify an existing command sequence, enter in the banner a 'U' in the Action field, the desired Application ID, and the Command Sequence Name. Modify the command sequence Description and/or enter (or change) Command IDs.
To delete an existing command list, enter in the banner a 'D' in the Action field, the desired Application ID, and the Command Sequence Name.
To add, modify, or delete a command list, the Application ID must exist and the operator's desk must be an APPLICATION-OWNER for the application entered. Any desk, however, that has access to the Command SeQuence function may view any command sequence in any application.
A Command Sequence Name must be unique within a given application.
There are three distinct groups of users for this system, Computing Services,the application administrators, and the departmental desk administrators. The following procedures will be required by each group to use the NSM-MS System.
First, Computing Services will design the online application to conform to the requirements of the NSM Architecture. The functional specifications available for the NSM Architecture provide the necessary information. Also, Computing Services will be responsible for adding and maintaining Users, Applications, and Application Menu Command data on the Natural Secured Menu files via the NSM-MS System. Finally, Computing Services will enforce security within each application command by designing and coding the appropriate restrictions into the function module programs.
Departmental desk administrators will be responsible for defining and maintaining desks under their budgetary unit(s). The assignment of individuals to those desks is also a responsibility of the desk administrator.
Each NSM application administrator will be responsible for establishing and maintaining the security data required by the application via the NSM Maintenance System. This will include establishing and maintaining valid Application-Desks, Command-Security-Groups, and Value-Security-Groups. The owner will be responsibile for maintaining application default access availability and the associated default security definitions for such access. Also, the administrator will be allowed to Lock/Unlock Applications and Command-Security-Groups as well as enter the associated reason/messages. Last, the administrator can maintain an Application-Notice to communicate pertinent information to all Users that logon to their application.
| U | User maintenance |
| A | Application maintenance |
| M | application Menu maintenance |
| D | Desk maintenance |
| UD | User Desk maintenance |
| CS | application Command Security maintenance |
| VS | application Value Security maintenance (optional) |
| AD | Application Desk maintenance |